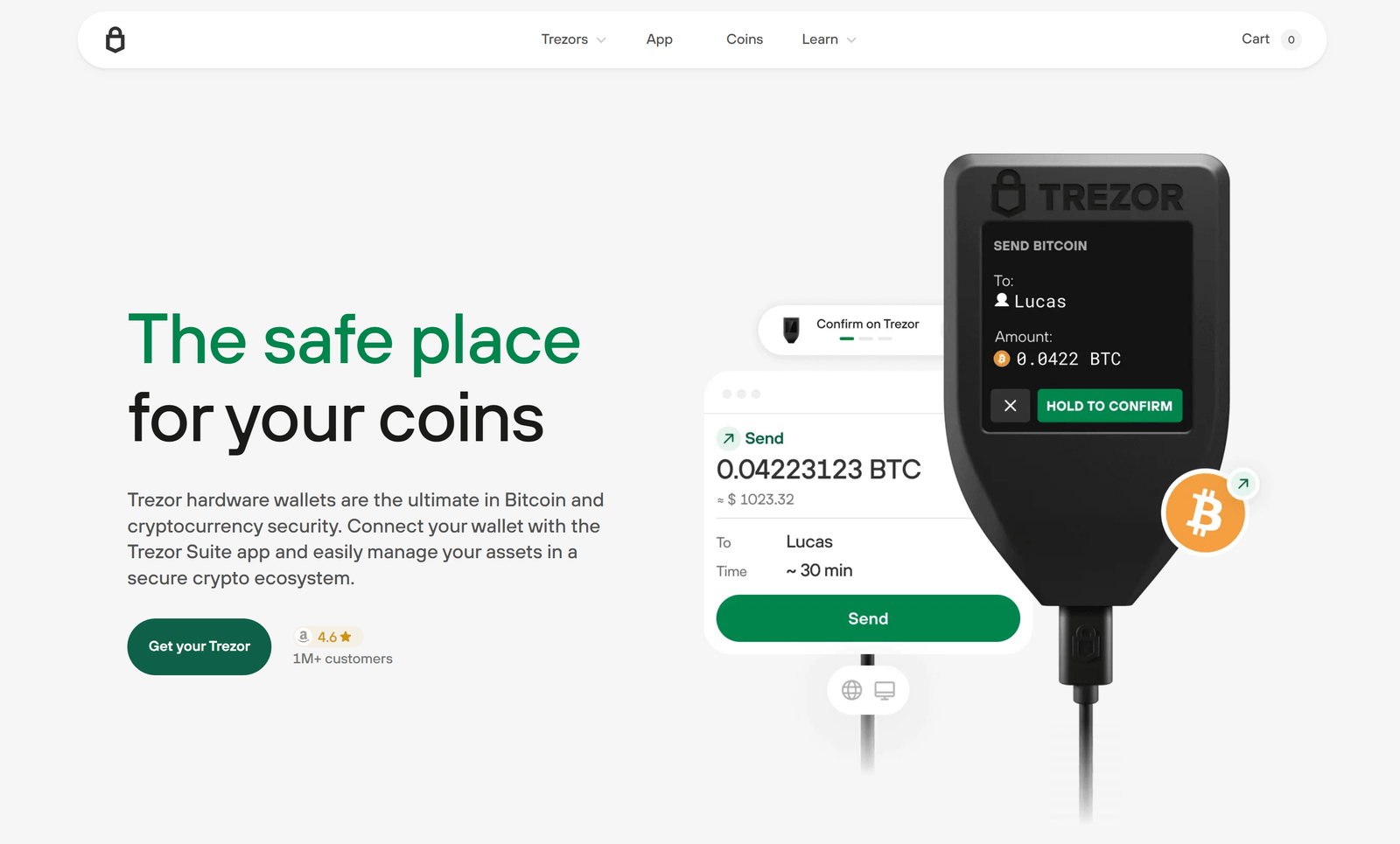
Overview
Trezor Bridge acts as a local bridge between the Trezor device and apps running in your browser or on your desktop. It handles USB / WebUSB interactions, session management, and request forwarding while ensuring that private keys and signing authority remain on the hardware device. Bridge is intentionally minimal — it does not store secrets and only transmits the public data needed to display accounts and construct transactions.
Download and Installation
Always download Trezor Bridge from the official source: trezor.io/start. Official installers are available for Windows, macOS, and Linux. Verify the platform-appropriate installation instructions and checksum or signature if these are provided. Installing only the officially distributed Bridge prevents tampered versions that could undermine your device security.
During installation, Bridge requests only the permissions necessary to access USB devices and to run as a background helper. It is designed to be low-impact and to start when required by supported apps.
How Bridge Works
Once installed, Trezor Bridge runs as a local background service listening for connections from verified web pages or desktop clients. When a supported app requests access, Bridge mediates the request and forwards it to your connected Trezor device. The device displays transaction or account details on its screen and requires your explicit approval to sign. This clear separation between host application and hardware signing is the core security property of the Bridge architecture.
Security Practices
Trezor maintains a security-first model: private keys and seed words never leave the hardware. Bridge communicates only non-sensitive information and requires device confirmations for all signing actions. To maintain a secure environment, follow these practices:
- Download Bridge only from trezor.io/start and verify integrity where possible.
- Confirm all transaction details on the Trezor device display before approving.
- Keep Bridge, Trezor Suite (if used), and device firmware up to date via official channels.
- Use a trusted host machine for custody or high-value operations and minimize untrusted browser extensions.
Privacy Considerations
Trezor Bridge transmits minimal information required for account display and transaction building. It does not collect or transmit seed phrases or private keys. Users concerned about metadata can employ network-level protections, adjust application telemetry settings, and minimize address reuse to reduce on-chain linkability. Review Trezor Suite and supported applications' privacy settings for the best control over telemetry and diagnostics.
Troubleshooting Common Issues
Connectivity issues are commonly resolved with a few checks: ensure your device is connected and unlocked, try a different USB cable or port (prefer direct ports over hubs), restart the Bridge service or the host machine, and confirm that no other process is blocking access. If using a browser, ensure it supports WebUSB and that no extensions are interfering. When problems persist, reinstall Bridge from the official site and consult published diagnostic guidance.
Enterprise & Advanced Deployment
For organizations, Bridge can be part of a hardened endpoint strategy: use dedicated management workstations, limit network exposure, and combine Trezor devices with multi-signature or HSM-backed workflows where appropriate. Maintain strict operational playbooks for device provisioning, transfer, and decommissioning to minimize insider and supply-chain risks.
Conclusion
Trezor Bridge is a compact but critical component that enables secure, reliable communications between Trezor hardware wallets and the apps you use to manage crypto. When obtained from official sources and maintained with appropriate host hygiene and device verification, Bridge offers a dependable layer that preserves on-device signing and strong self-custody principles.